Definition
A session ID is a unique number a server assigns to requesting clients. ID stands for identifier and is used to identify and track user activity. This unique ID can be a number code, numerical code, or alphanumeric code. In computer science, a session is a temporary connection between server and client.
The short version SID (session ID) is also commonly used, for example in the context of web servers.
In the field of search engine optimization (SEO), session IDs are a relevant topic as under certain circumstances they can cause problems with duplicate content.
Methods of transmitting session IDs
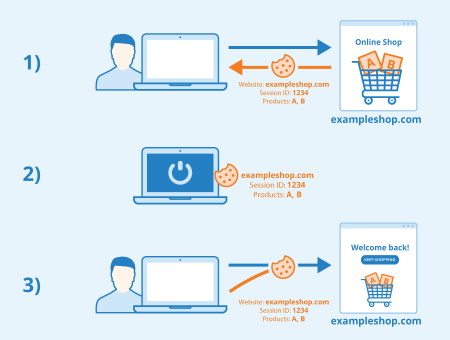
Cookies
If a user visits a website such as an online store, the store server generates an individual session ID assigned to exactly that visitor and that session. This session ID is stored locally on the visitor’s computer within a cookie (also called “session cookie”). If he sends a new request to the server during the session, the cookie with the assigned ID is transmitted along with the request so that the server can assign the communication to the corresponding user.
If that visitor leaves the shopping cart in order to look at other products in the store or even to close the store, the cookie ensures that the session won’t get lost. This way, the shopping cart can be restored as soon as the user returns to the website.
The products in the shopping cart are assigned to the session ID and stored in the session cookie. Each request to the server and each response to the user has to be accompanied by exactly this session ID. Otherwise, a new ID is assigned with the next client request, and the old session is lost.
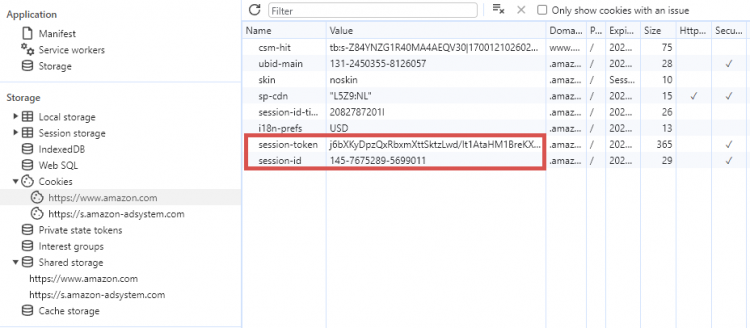
Example of session cookies on Amazon.com
URL parameter
If the user disabled the storage of cookies in advance, for example by using the function “deactivate cookies”, the session ID can be transferred from the server to the browser as a parameter attachment to the URL of the store page. This parameter allows a server to recognize and create sessions, which means that information such as shopping carts or similar can be retrieved again as they are linked to the session.
Example of a URL with session ID attached as a parameter:
https://www.example.com/index.php?sid=123454321abcde-54321dcba
The web programming language PHP is able to identify and assign this link. Thus, the shopping cart connected to this session can be retrieved again.
Hidden Form Field
Another form of tracking user behavior is the Hidden Form Field, allowing data to be sent to the server that cannot be seen or changed by the user. For example, a hidden form field can transmit information about which database entry is to be updated. This method can also be used for transmitting session IDs from browser to server.
Use Cases of Session IDs
There are a number of common use cases for session IDs, some of which include:
- User authentication: Session IDs are crucial in maintaining user sessions post-login, ensuring that users stay authenticated as they navigate through different parts of a website or application.
- Shopping carts in E-commerce: They keep track of items a user has added to their cart, even if they navigate away from the page.
- Personalization: Websites use session IDs to remember user preferences and deliver a personalized experience.
- Analytics and tracking: They help in tracking user behavior on a website, which is vital for analytics. This also allows webpages and features to be customized to the user.
- State management in web apps: Session IDs help keep track of user activities and choices in web applications, particularly when the communication between the user’s device and the server does not automatically remember previous interactions.
Session Management Best Practices
There are several common best practices to ensure the secure and efficient use of session IDs. Some best practices for session management are:
- Secure session ID generation: Use strong, random methods to generate session IDs to prevent predictability.
- Session expiration: Implement session timeout and expiration policies to reduce the risk of unauthorized access.
- Cookie security: If session IDs are stored in cookies, ensure they are marked as secure and HttpOnly to prevent access via client-side scripts.
- Preventing session fixation: Regularly regenerate session IDs, especially after login, to prevent session fixation attacks.These attacks occur when an attacker hijacks a user’s session by stealing or fixing the session ID
- Data encryption: Use SSL/TLS encryption to protect session data during transmission.
- Monitoring and Logging: Keep track of session creation, expiration, and anomalies to detect potential security threats.
Session ID and SEO
Using URL parameters to transmit session IDs can lead to duplicate content because Google can find and index the resulting URLs. If different users access the same product or category page, thus generating different parameter attachments of the URL, yet reaching identical content, there is a risk that Google will classify this content as duplicate content. This is important to keep in mind for SEO. However, Google does not actively rank the website in question lower – the relevance of the respective subpage is rather distributed among the numerous URLs with different session IDs. This in turn can have a negative effect on the website’s ranking on Google.
From an SEO perspective, transmitting session-IDs via URL parameters can thus be problematic and should be avoided. If this is not possible, the problem can be solved by using a canonical tag. This way, Google will be signaled that the URL without session ID is the original resource intended for indexing, while URLs with a session ID are not indexed.
Session IDs should not be seen as mandatory and should only be used if they are useful for the site visitor and/or site operator.
Session cookie and GDPR
The General Data Protection Regulation (GDPR) has been in force in the EU since May 25, 2018. It does not explicitly regulate the use of session cookies. However, Article 6 of the GDPR states that prior consent to the use of cookies is not necessary if the cookie is required to protect legitimate interests of the person responsible or a third party. Session cookies can also be classified as such. Therefore, the use of session cookies should be specified in the privacy policy.
Security
The use of session IDs is considered relatively safe. However, by manipulating stored session IDs in the browser it is theoretically possible to get the session ID of a third user. This is extremely unlikely if the server that generates individual session IDs draws from a sufficiently large spectrum of codes that are neither sequential nor easy to guess. Apart from this, online shops in the EU often use SSL encryption, which provides an additional level of security. A match would therefore be highly unlikely.
The situation is different when malicious code is intentionally implemented. If an attacker inserts such code into a webshop system via Cross-Site-Scripting (XSS) and a user executes the code via the website, the ID could be transmitted and the entire session could be hijacked, i.e. redirected. The attacker would thus have access to certain customer data and could in turn make an order on behalf of the user.
Alternatives to session ID
While session IDs are widely used, there are alternative methods for user identification and session management.
- Tokens (such as JWT – JSON Web Tokens): Unlike session IDs that are stored on the server, tokens are stored client-side and contain user information and permissions. This approach offers better scalability as it reduces server load, but it can be less secure if the token is intercepted, as it contains user data.
- Cookies: While session cookies are one way to store session IDs, other types of cookies can also be used for user identification without involving server-side sessions. These cookies are easier to implement and manage but can be less secure, as they are susceptible to client-side attacks like cross-site scripting (XSS).
- Local storage: For less sensitive data, web applications might use local storage for session management, although this method lacks server-side control. It provides a simple way to store data on the client’s browser, but it’s not suitable for sensitive information due to its vulnerability to cross-site scripting attacks.
- OAuth: This is a more complex method used primarily for authorization, allowing users to authenticate with third-party services without exposing their credentials. While OAuth provides a high level of security and is ideal for interactions with third-party services, it can be complex to implement and requires a thorough understanding of security protocols.
Related links
- https://auth0.com/blog/what-is-broken-authentication/
- https://www.tutorialspoint.com/php/php_sessions.htm
Similar articles
